한국리눅스유저그룹 - LUG KOREA 한국리눅스유저그룹 - LUG KOREA
|
토크박스/가입인사 | SW/HW 사용기 | LUG 위키 | wiki 영어공부 | 사이트맵 | 즐겨찾기 | Home | ||||||
[메일링리스트] -
Slashdot |
Kernel News |
GNOME |
KDE |
linux.kernel |
C++ |
wxWidgets |
Java |
Python |
Android

|
|||||||
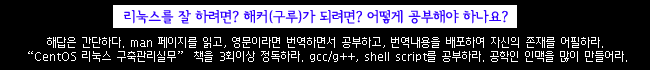
| 구인/서버,개발자 | 장터 | 리눅스 QA | JSP & JAVA 입문 | 쉘 스크립트 입문 [오타]| gcc/C++ 입문 | CentOS 리눅스구축관리실무 [오타], [찾아보기] | |||||||
|
|||||||
|
|||||||
|
|||||||
|
||||||||||||||||||||
|
한국LUG는 대한민국의 리눅스 지식인[사용자/개발자]들의 커뮤니티입니다. [매년 1~2회의 공개세미나 개최]
한국LUG : 울산 - 광주 - 전북 - 인천 - 대전 - LUG 위키 [Linux Distribution] : CentOS | Ubuntu | Fedora | WhiteBox | Debian | Slackware | Gentoo | openSuSE "Linux" is a registered trademark of Linus Torvalds. "Linux is Kernel" - 리눅스는 공짜가 아니라 자유[Free & Effort]입니다 - |
|||||||||
| [인터넷 서점/출판사 링크] : 강컴 | 알라딘 | 인터파크 | 예스24 | 교보문고 | 수퍼유저코리아 | 제이펍 | |||||||||
| 한국LUG 사이트는 1024 x 768 해상도(운영자 노트북:14")에 최적화 되어 있습니다. : LINUX FANSITE WWW.LUG.OR.KR Server is made by CentOS Linux, P4 1.8G, Memory 512MB, Main HDD 160GB, Backup HDD 40GB and LAMP, qmail MTA. |
|||||||||
| |||||||||
|
LUG 포인트 정책 : [회원가입 : +100점] [로그인(하루한번) : +100점] [글쓰기 : +20점] [코멘트 : +10점] [다운로드 : -200점] [질문 포인트 : 최소 200점] 데스크탑 프로그래밍(gcc, g++, wxGTK[wxWidgets] 등)은 "Fedora"를 사용하고, 서버 운영(WEB, FTP 등)은 "CentOS"를 사용하시길 권장합니다. 도전하는자, 자신을 투자하는자만이 뜻하는바를 이룰 수 있다. Information should be Exchanged with Interactive, not One Way Direction.  준회원, 준회원,
 정회원, 정회원,
 우수회원, 우수회원,
 VIP회원, VIP회원,
 기업회원, 기업회원,
 관리자 관리자Be Maker! |
|||||||||
|
인생에서, 100% 순이익을 보장하는건 없다. 1%의 지식을 나눔으로써, 가끔씩 손해볼 필요도 있다.
그대가 가진 1%의 지식만이라도 공공을 위해 포스팅하라. 손해본다는 생각이 앞선다면 그대의 인생은 힘들어질것이다. 자신이 가진 지식의 1%도 투자하지 않고, 오로지 자신의 이익만 탐하는자와는 동지가 되지마라. 만나서 대화하면 모두 좋은 사람들이지만, 유독 인터넷에서만 자신을 밝히지 않고, 좀비로 서식하는 사람들이 많다. 부지불식간[不知不識間], 좀비(하류) 인생이 될지도 모르니, 항상 자신을 경계하도록 하라. |
|||||||||